AMOS is a stealer that targets macOS users, with a fairly wide range of functionality. Recently, we saw many variations of this malware, including Poseidon, Odyssey, and Banshee.
Once the device is infected, a fake pop-up window is displayed requesting access to system settings and asking the user to enter their password. This social engineering technique allows the malware to obtain the system password.
After that, the following device data is collected: device model, UUID, processor, RAM, and OS version. It also requests access to user folders such as Desktop and Documents to download user files.
In addition, the stealer can obtain data from Keychain (a password storage and management system on macOS that stores credentials, usernames and passwords for websites, credit card details).
By elevating system privileges through a fake system window, the stealer can obtain root privileges and install additional malicious modules.
The malware performs the following actions in the system:
The code mentions the following browsers:
- Firefox (parseFF function)
- Chromium (chromium function)
The malware analyzes the profiles of these browsers, copying files such as cookies.sqlite, logins.json, key4.db for Firefox and Cookies, Web Data, Login Data for Chromium.
A list of browser extension IDs has been discovered, including known cryptocurrency wallets that the malware targets:
Malware attempts to access browser extension files, including cryptocurrency wallets; accessing wallet files could allow the theft of private keys or login credentials.
The collected data is sent to a remote C2, which was discovered by examining network connections using Wireshark.
A C2 server (Command and Control Server) is a server used to remotely control compromised devices or malware.
HTTP/HTTPS is used to communicate and send stolen data to the C2 server, which can complicate the analysis of suspicious traffic due to the large amount of legitimate traffic and encryption when using SSL.
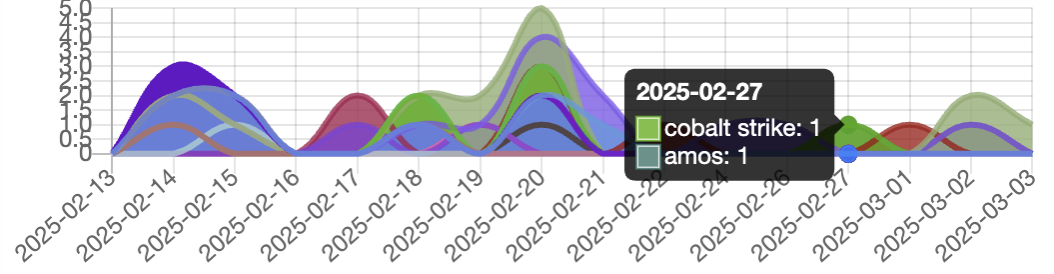
A new variation of the AMOS malware was recently discovered in the malware app.
The graph below shows the malware’s activity over the recent period.
After analyzing the AMOS threat it was found that the IP is located in one of the Eastern European countries and at the time of the research the server is active.
You can see more details in the image below.
After examining the IP, a large number of domain names were discovered with the stealer.
During research domain names were active and ready to interact with infected devices.
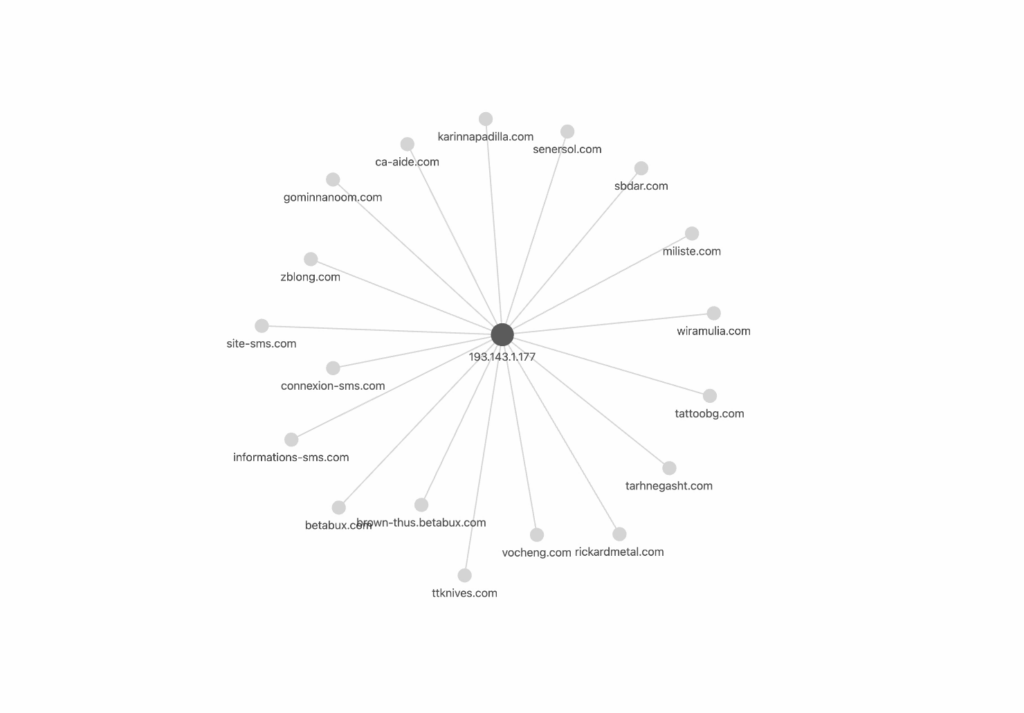
All these domains have common characteristics – the use of free SSL certificates Let’s Encrypt and domain names that at first glance are legitimate and may resemble well-known resources.
Some of the certificates, although they have expired, can still receive and transmit data from a remote C2.
IoCs
File
4518666c9dcb3b71268097a6458feb1dbfa4d2dff159b0fb613f6681187aa227
IP
193.143.1.177
ASN:198953
ISP:Proton66 OOO
Domain
- rickardmetal.com
- ca-aide.com
- site-sms.com
- vocheng.com
- zblong.com
- miliste.com
- wiramulia.com
- sbdar.com
- senersol.com
- betabux.com
- tattoobg.com
- ttknives.com
- gominnanoom.com
- tarhnegasht.com
- informations-sms.com
- karinnapadilla.com
- brown-thus.betabux.com
- connexion-sms.com
Top 10 Browser extensions
- keenhcnmdmjjhincpilijphpiohdppno
- hbbgbephgojikajhfbomhlmmollphcad
- cjmkndjhnagcfbpiemnkdpomccnjblmj
- dhgnlgphgchebgoemcjekedjjbifijid
- hifafgmccdpekplomjjkcfgodnhcellj
- kamfleanhcmjelnhaeljonilnmjpkcjc
- jnldfbidonfeldmalbflbmlebbipcnle
- fdcnegogpncmfejlfnffnofpngdiejii
- klnaejjgbibmhlephnhpmaofohgkpgkd
- pdadjkfkgcafgbceimcpbkalnfnepbnk
Links:
https://app.malwareleaks.com/ipv4all/193.143.1.177/443
Have a question?
Contact us with your issue, and we’ll gladly assist you.