An API key is a unique identifier used for authenticating and authorizing the malwareleaks app when interacting with the API.
How to get an API key?
To obtain an API key, follow these steps:
- Contact with Support team for register at https://www.malwareleaks.com/contact-us/
- Once registered, an account will be created, and the API key will be generated in the Profile – API section.
- After receiving the key, make sure to store it in a secure location.
How to use the API key?
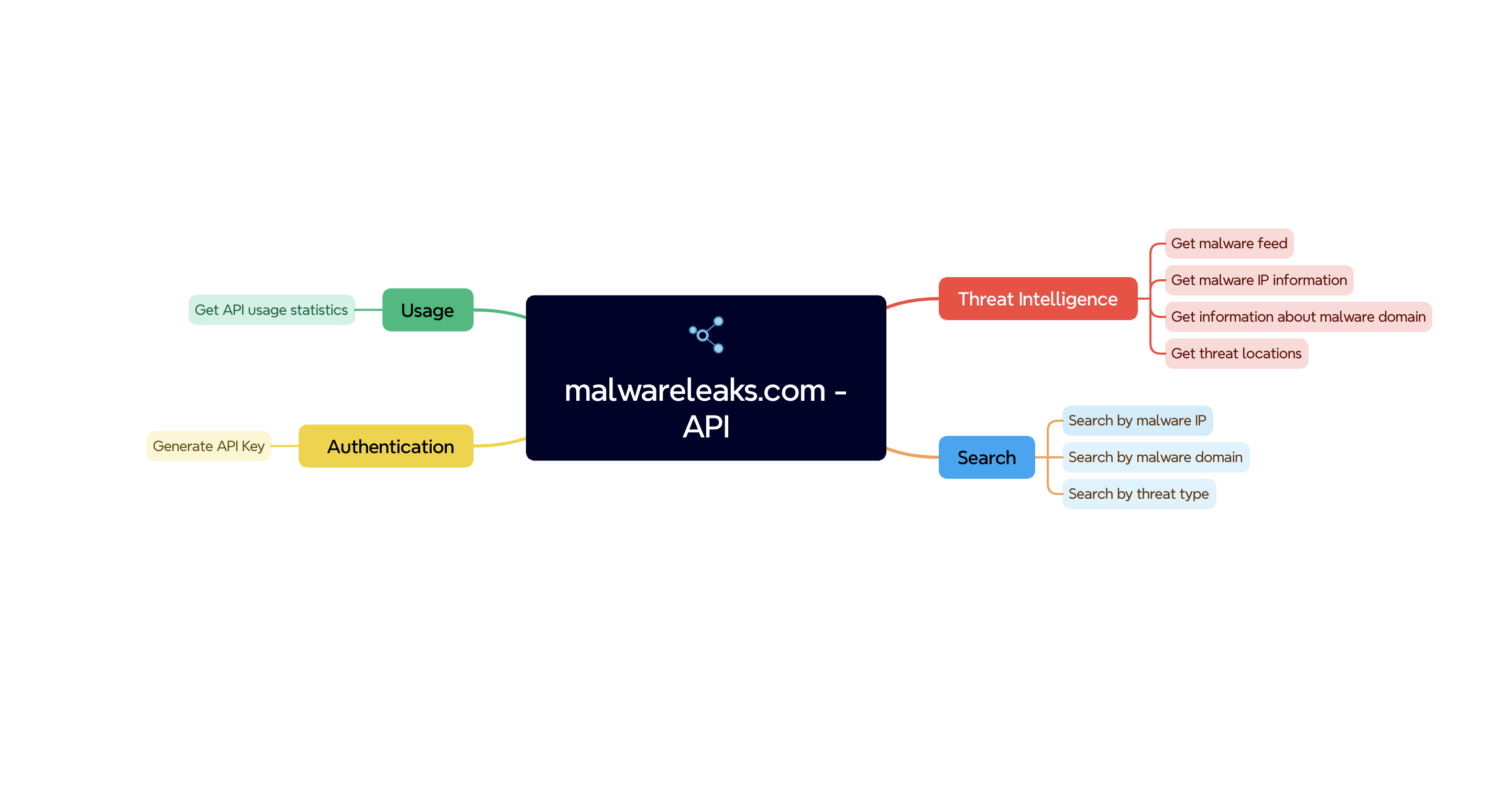
Authentication
This section refers to the process of verifying the identity of the user or accessing the API.
It ensures that only authorized users can interact with the platform.
- Generate API Key: This action involves creating a unique API key for the user.
Usage
Tracks and displays information about the usage of the API.
- Get API usage statistics: This feature allows users to view statistics related to their API usage.
Threat Intelligence
This section provides valuable insights into cyber threats.
- Get malware feed: This feature provides users with a continuous stream of information regarding threats, including newly discovered.
- Get malware IP information: This function allows users to retrieve details about IP addresses.
- Get information about malware domains: This feature provides information about domains that are associated with threat activity.
- Get threat locations: This service provides data about the geographic locations of threats or attacks.
Search
This section allows users to search for specific information related to malware, IPs, domains, and threat types. It’s a key tool for investigation and threat analysis.
- Search by malware IP: This feature allows users to search for information related to specific IP addresses that are associated with threat activity.
- Search by malware domain: This function enables users to search for domains related to threat.
- Search by threat type: This feature allows users to search for information on specific types of threats (e.g., AMOS, GoPhish, Cobalt Strike, Metasploit Framework, etc.).