Python is a high-level programming language that is well-known for its readability, ease of use, and broad support for a variety of applications, including artificial intelligence, data science, and web development.
Within the Python community, the Python Package Index (PyPI) is an essential repository for software packages that speed up application updates and development.
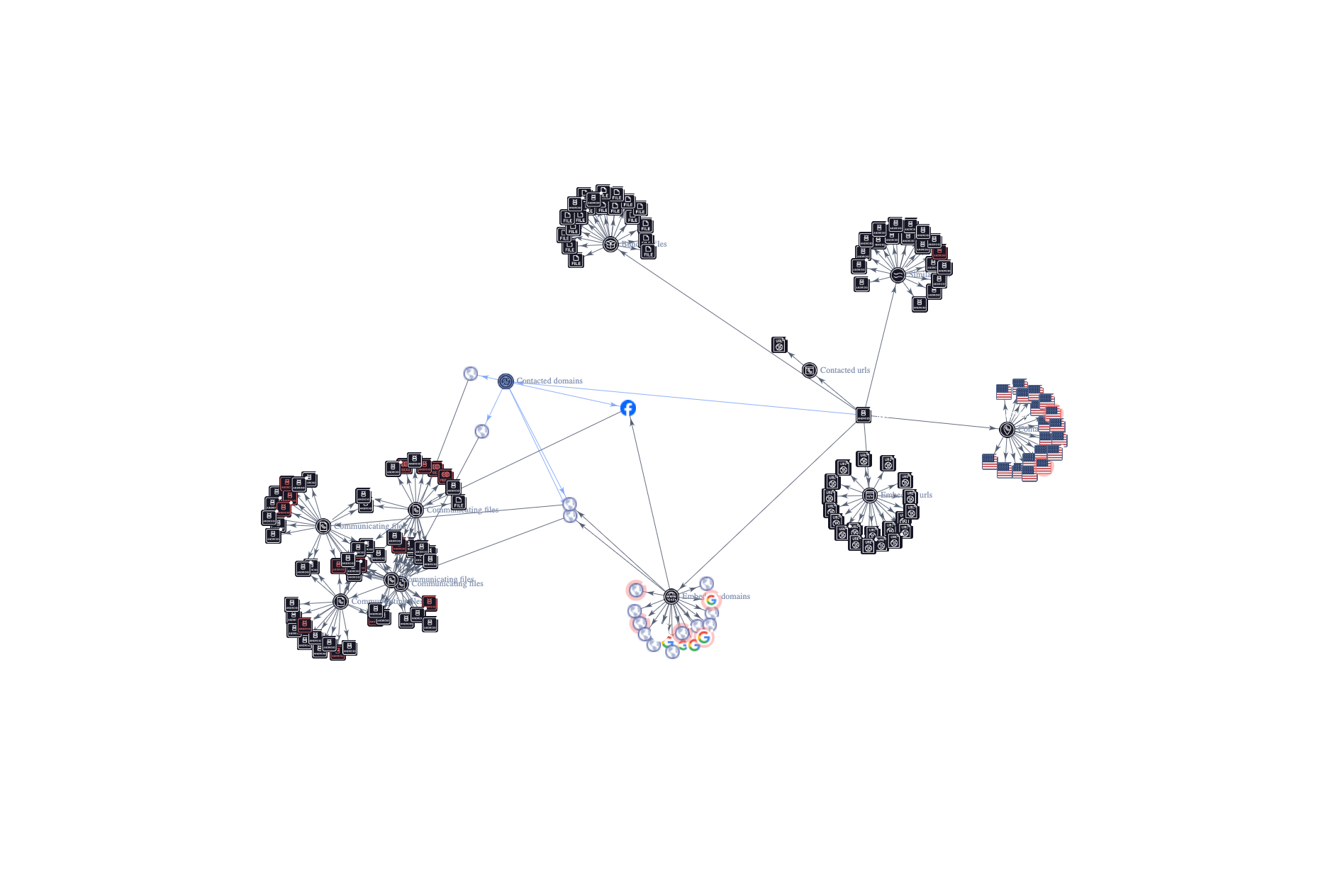
Malwareleaks recently identified that malware author “WS” has covertly uploaded several malicious packages. These packages use Python setup.py files with base64-encoded source code, which triggers malicious payloads to be executed upon installation. These attack methodologies resemble a campaign from early 2023.
Users should be cautious when using open-source packages due to the adaptable threats of MITRE ATT&CK tactics, which include using different IP addresses for data transmission and targeting Windows users.
An instance of this can be found in the “sGMM” package, where the PyInstaller tool is used by the Python-compiled executable to maintain an unobtrusive profile by discreetly monitoring instances.
Another example uses the “myGens” and “NewGends” packages, which circumvent Windows Defender by connecting to a malicious IP and using an encrypted VB.NET executable to gather data.
When the “TestLibs111” package runs, encrypted traffic to a dubious IP address is visible, showing that confidential data may have been exfiltrated.
The thorough analysis highlights the increasing risk of information-stealing malware and highlights the necessity for users to exercise caution and implement deliberate safeguards when interacting with free software in order to guard against persistent and ever-changing adversaries.